configure manager add 192.168.1.6 firepower show managers Type: Manager Host: 192.168.1.5 Registration: Completed ciscoasa# show service-policy Global policy: Service-policy: globalpolicy Class-map: global-class SFR: card status Up, mode fail-open. Next we need to add managers on FTD: (vFTD can be only managed via FMC) show managers No managers configured. configure manager add 150.1.7.200 123456 show managers Host: 150.1.7.200 Registration Key:. Registration: pending RPC Status: Type: Manager.
- Firepower Configure Manager Addon
- Firepower Configure Manager Add Dontresolve
- Firepower Configure Manager Delete
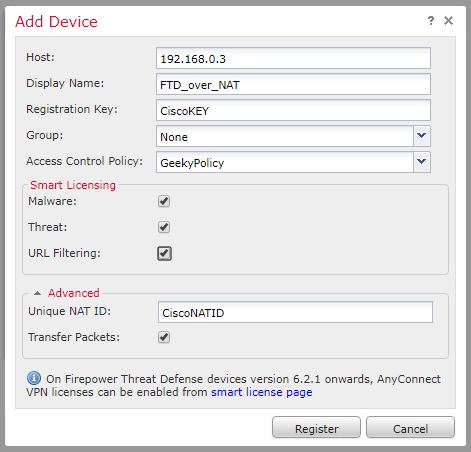
Firepower Threat Defense Active/Standby Failover 1. Firepower Threat Defense High Availablity Active/Stanby 2. On FTD-1 and FTD-2, access the CLI and configure the FMC 192.168.111.20 as a manager using the configure manager add 192.168.111.20 cisco123 command. On FMC, under Device Management, register both devices on FMC.
The goal of this article is to quickly show you how you can configure your Firepower Management Center (FMC) to authenticate against Active Directory.
- First login to FMC as a local admin
2. Hover over System, then select Users
3. Select External Authentication
4. Select Add External Authentication Object
5.1 Set the Authentication Method to LDAP, give the object a name (can be anything), set the server type as MS Active Directory
5.2 Set your Primary and Backup AD server (ideally your environment should have two Domain Controllers at a minimum that are on different hardware and disks)
5.3 Here we will set our base DN for the domain, then an LDAP filter to only allow domain admins. Finally we will finish it off by setting up a Firepower service account in AD (does not need to be an ADMIN, just needs to be able to read objects)

Base DN = dc=domain,dc=local
Base Filter = (memberOf=CN=Domain Admins,CN=Users,dc=domain,dc=local)
Username = CN=fire power,CN=Users,DC=domain,DC=local
Note: In production you should make sure to set up a self signed cert on the DC so that the LDAP session is encrypted. If you were to leave encryption off, a man in the middle attack could grab your AD account and wreck havoc.
Firepower Configure Manager Addon
5.4 Now we need to set our attribute mapping in FMC. This will be what the the admin types in to login, I chose sAMAccountName for consistency. UPN did not work well for me so I used this.
5.5 The group controlled access roles are if we want to get granular and assign FMC membership of tiers. In my setup I only need domain admins to be able to access FMC as admins, so I did not need to set this up. I left all of these blank, even the default user role.
5.6

The Shell access filter (linux shell) is set to the same as the base filter, you don’t have to do this if you don’t need shell access.
5.6 Go ahead and save this.
5.7 After clicking save it should have taken you one page back into the FMC external authentication page. We now need to save and apply our settings to the FMC.
5.8 Click apply here too
5.9 Now log out and test it!
6 Wohoo that worked!
Head back into the external authentication page where we set all of this up to view your new user profile.
The FMC creates a mapping for every user that logs in externally.
Troubleshooting:
The most common problem I foresee with AD authenticated FMC is people mistyping their DN’s so please double check those in section 5.3
Back in the external authentication object, if we edit we can go back in and use the test button.
Scroll all the way to the bottom of the page and input some domain admin credentials to test with.
The page refreshes and we see this:
If we scroll all the way to the bottom we can check the verbose test log.
You have the FMC installed and connect to FTD device with configuration deployed but for what ever reason there is a problem and you need to enter the CLI on the Firepower device to troubleshoot the equipment and although you can’t configure anything you can do show and debug commands to troubleshoot via the CLI.
Firepower Configure Manager Add Dontresolve
We have to enter the Diagnostic CLI and we can do this in two ways:
- Once logged into the Firepower default prompt type system support diagnostic-cli command.
Firepower Configure Manager Delete
- The other way is to go into expert mode followed by using the sudo lina_cli command.
If we look at the show version we can see in this example we are running ASA code with FXOS running with it.
If you worked in the Cisco ASA world before you might find the CLI a refreshing memory because all of your debugs, show outputs and the packet tracer troubleshooting tool are all there. You might be asking well its good to see the configuration but how do I configure something that may not be in the FMC? Well we can use something called FlexConfig and is available from FMC 6.2.0 and onward.
