Group-policy Profile-SSL-VPN internal group-policy Profile-SSL-VPN attributes vpn-simultaneous-logins 4 vpn-idle-timeout 10 vpn-session-timeout 60 vpn-tunnel-protocol ssl-client ssl-clientless split-tunnel-policy tunnelspecified split-tunnel-network-list value Split-Tunnel default-domain value xxxxxxxxxx.com address-pools value SSL-VPN-POOL. Split-tunnel-policy tunnelspecified split-tunnel-network-list value splittunnel default-domain value domain.internal username admin password xxxxxxxxxxxxxx encrypted privilege 15 username vpn1 password xxxxxxxxxxxxxx encrypted username vpn1 attributes service-type remote-access.
- Ipv6-split-tunnel-policy Tunnelspecified
- Cisco Split-tunnel-policy Tunnelall
- Split-tunnel-policy Tunnelspecified
Split tunneling controls what traffic is or isn’t protected by the tunnel. By default the Easy VPN server forces the client to tunnel all user traffic to the server; you can ease this restriction and define split tunneling policies for your users, which your server downloads to the remote and which the remote enforces.
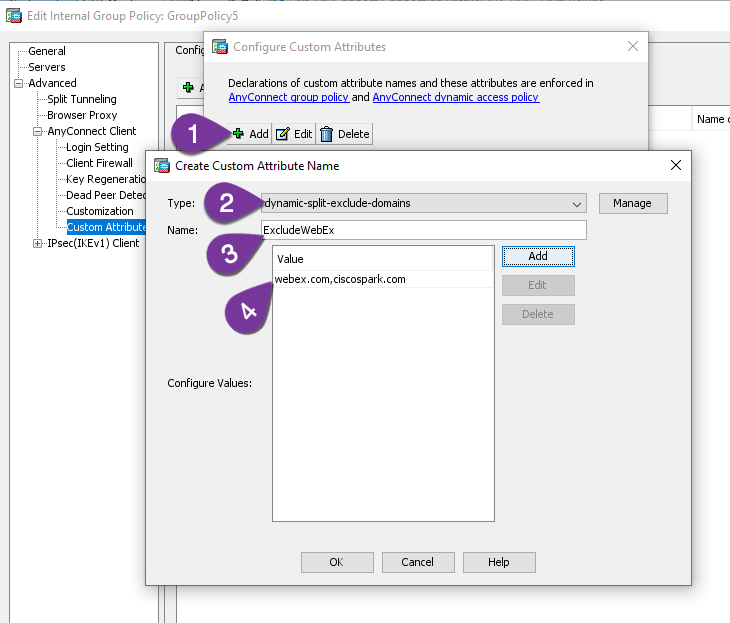
Split tunneling defines what traffic from the user must go across the tunnel and what traffic can leave the client in clear text. Split tunneling policies are defined with the split- tunnel-policy command. The default split-tunneling policy is tunnelall, which means that, with the exception of DHCP and ARP packets, all traffic from the remote must go across the tunnel. You can exclude networks from being tunneled (excludespecified parameter) or include networks that should only be tunneled (tunnelspecified parameter). When overriding the default split tunneling policy, you must use the split-tunnel-network-list command to specify what destination networks are (tunnelspecified) or are not tunneled (excludespecified). These are defined in an extended or standard ACL. For a standard ACL, the addresses or networks you enter are addresses that the remote is trying to reach (destination addresses). For an extended ACL, the addresses off of the higher-level interface of the appliance (corporate office networks) are the source addresses in an ACL statement, and the destination addresses are the internal addresses of the remotes.
Ipv6-split-tunnel-policy Tunnelspecified
Also, if you have split tunneling disabled (the default), this means that all remote access traffic has to come to the appliance first, before it goes anywhere else, including the Internet. In this case, the appliance by default drops traffic that enters and leaves the same interface. To allow this behavior, configure this command:


Cisco Split-tunnel-policy Tunnelall

Split-tunnel-policy Tunnelspecified
ciscoasa(config)# same-security-traffic permit intra-interface
